Phishing scams try to trick you into revealing sensitive data or downloading malware, often leading to identity theft, credit card fraud, or other cybercrime. Learn all about phishing and how to prevent it.
With billions of phishing emails sent daily, phishing is one of the main ways online fraudsters attack individuals and organizations.
In 2022, the FBI received over 800,000 complaints of internet crime in the US, resulting in an estimated total loss of $10.3 billion. Of these, over 300,000 were related to phishing(new window).
Successful phishing attacks can have devastating consequences. Scammers could steal your identity(new window), drain your bank account, or hit you with ransomware. If you run a business, that could also mean loss of intellectual property, customer trust, and reputation.
We explain what phishing is, how it works, and how to protect yourself against phishing attacks.
- What is phishing?
- How does phishing work?
- Types of phishing attacks
- How to spot a phishing email
- Three steps to check for phishing
- How to prevent phishing attacks
- Protect your business from phishing
- Stay safe against phishing
What is phishing?
Phishing is an online scam in which attackers send you a fake message (usually by email) to trick you into revealing sensitive information (like login or credit card details) or downloading malware(new window) on your device.
The message appears to be from a legitimate source, like a bank, an email provider, or a popular service like Amazon, PayPal, or Facebook. But the aim is to trick you into doing one of the following:
- Enter your personal details on a website that appears legitimate but in fact steals your data
- Click on a link to a malicious website or download an infected attachment that installs malware on your computer, tablet, or phone
- Reply to the message to provide sensitive personal data by email
A form of social engineering(new window), phishing messages often create a sense of urgency or excitement to make you respond without thinking.
How does phishing work?
Typically, phishing messages contain urgent requests, threats, or prizes asking you to take immediate action. For example, they may claim your Amazon account has been “suspended” and you need to “confirm” your account details to reactivate it.
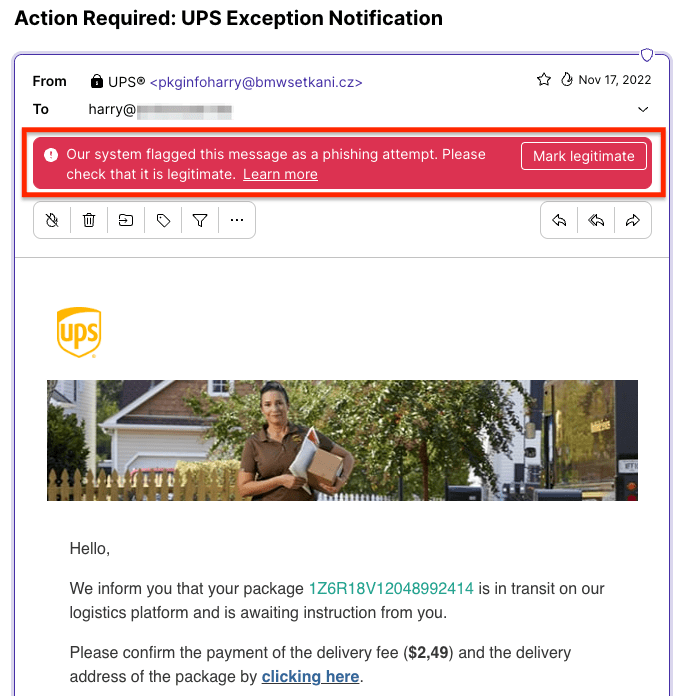
In this phishing email, which appears to be from the delivery service UPS, you’re asked to click on a link to pay a “delivery fee” and provide personal details. If you don’t, you won’t get your “package”.

But check the email’s From line, and you’ll see it’s not genuine. The display name says UPS but the following email address (@bmwsetkani.cz) clearly has nothing to do with UPS. In any case, you haven’t ordered any UPS delivery.
Clicking on the link could lead to a fake website where you’re asked to enter your credit card details, home address, or other sensitive data. Or the email could include an unsolicited attachment that automatically installs malware on your device when you download it.
See how to spot a phishing email below for more telltale signs of phishing.
Types of phishing attacks
Scammers can deliver phishing messages via SMS text, social media, or phone calls, but most phishing attacks come by email.
Email phishing
Attackers send bulk emails that appear to come from real organizations to trick you into revealing private information. Typically, scammers aim to steal account login details, banking or credit card details, or personally identifiable information to use for identify theft(new window).
Phishing emails are usually generic and sent in bulk as spam email. The more sent, the greater the chance of “catching” someone.
Spear phishing
Spear phishing emails are usually sent to specific people in an organization, often those with special access rights. The aim is to steal sensitive information like login details or to infect the victim’s device with malware to harvest confidential data.
Messages are often personalized and appear to come from a sender the target trusts, so it’s easy for them to let their guard down. For example, a fraudster impersonating a company accountant may email the accountant’s assistant asking them to make an urgent payment to a fake vendor.
Spear phishing is one of the main methods of business email compromise (BEC)(new window).
Whale phishing (whaling)
Like spear phishing, whaling is a personalized attack, but the target is top management, like a CEO. By targeting C-level management, the fraudsters hope to gain more valuable information or access to financial accounts.
As with spear phishing, targets can easily fall victim because the message may be highly personalized and convincing — apparently from someone they trust.
Vishing and smishing
Vishing is a kind of phishing that uses fraudulent phone calls or voicemails. Scammers pretending to be from a legitimate company call you (either a real person or robocall) and ask for personal information.
For example, they phone from your “broadband provider” and say there’s a problem with your account. They may ask for your name, Social Security number, or credit card information to “resolve the issue”.
Smishing is simply phishing that uses SMS texts instead of emails. Like phishing emails, the text may contain a malicious link to a fake website that’s used to steal your personal data. Or the link could download malware onto your device.
Angler phishing (social media)
Angler phishing is when scammers set up social media accounts pretending to be a company’s customer service agent. By intercepting a customer’s complaint or query on social media, they can ask the victim to provide personal details to “investigate the problem”.
Another method is to create a fake website resembling a social media login page. Fraudsters may also send you phishing emails that appear to come from a social network asking you to “update” or “confirm” your personal details.
How to spot a phishing email
While some phishing emails look like they’re from a legitimate source, many contain clear signs they’re fake.
Look out for the following red flags. Spot any of these in a message, and the chances are it’s a phishing attempt:
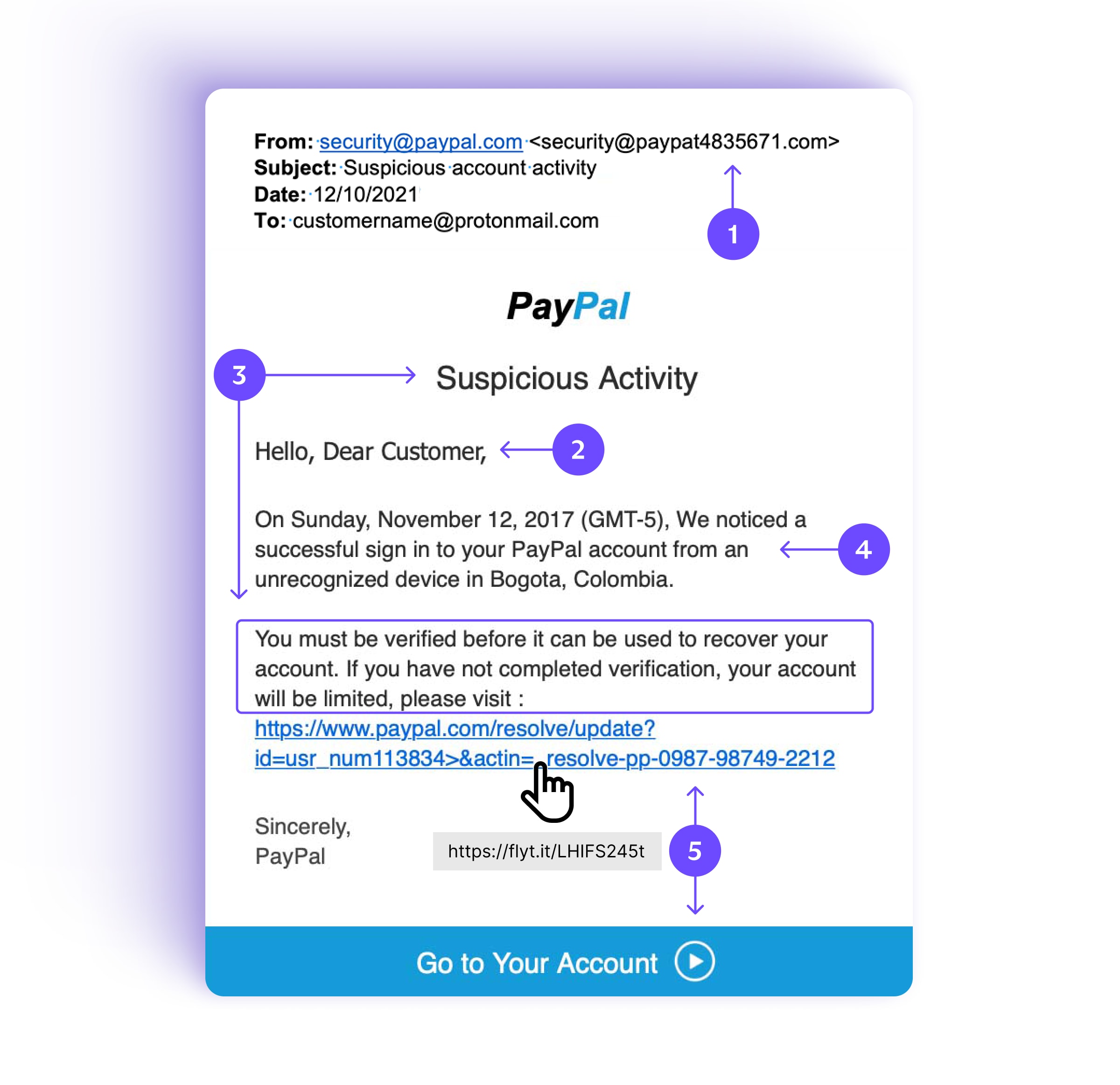
1. Unofficial sender’s address:
The sender in the From field is security@paypal.com, but the following email address is actually <security@paypat483576.com>. The unofficial address @paypat483576.com instead of @paypal.com is a good sign the message is fake.
2. Generic greeting
While legitimate emails usually greet you by name, like “Hi Alice” or “Hello Bob Jones”, fraudsters often start with a general greeting like “Dear Customer” or “Hi” followed by your email address. Or they may use no greeting at all.
3. Urgent requests, threats, or prizes
Phishing emails often pretend your account has been compromised. They ask you to take urgent action to “verify” or “confirm” your personal details, or your account will be suspended or closed.
Others report a pleasant surprise for you: a “tax refund”, “lottery win”, or “special offer” that’s only available for a limited time. Or a random beautiful man or woman on a fake adult site has picked you for a partner out of the blue.
4. Grammar or spelling mistakes
Scammers are not always the best writers, so look out for errors. Here it’s a simple capital letter “We” in the middle of a sentence, or it may be a company name misspelled: “Pay-pal” instead of “PayPal”.
5. Links, buttons, or unsolicited attachments
Phishing messages often invite you to click on a button or link to enter personal information or make a payment. If you’re using a computer, hover your mouse over the link (don’t click!), and you’ll see the URL (https://www.flyt.it) is different from the link (https://www.paypal.com).
Or messages may contain an attachment, like a fake invoice, containing malware that infects your computer when you download it.
Remember that some phishing emails may look completely normal; the only clue would be the suspicious intent.
For example, suppose you were a company accountant and “your boss Sally” (a fraudster) emailed you to make an urgent wire transfer to an unfamiliar bank account. The email looks like it’s from Sally, but would she do that? Is that her writing style? If in doubt, call or text her.
Three steps to check for phishing
All the above are clear indications of phishing, but not all scam emails are so easy to spot.
That’s why we recommend taking the following steps when you receive any email with a button, link, attachment, or request for personal details, especially if it’s demanding urgent action:
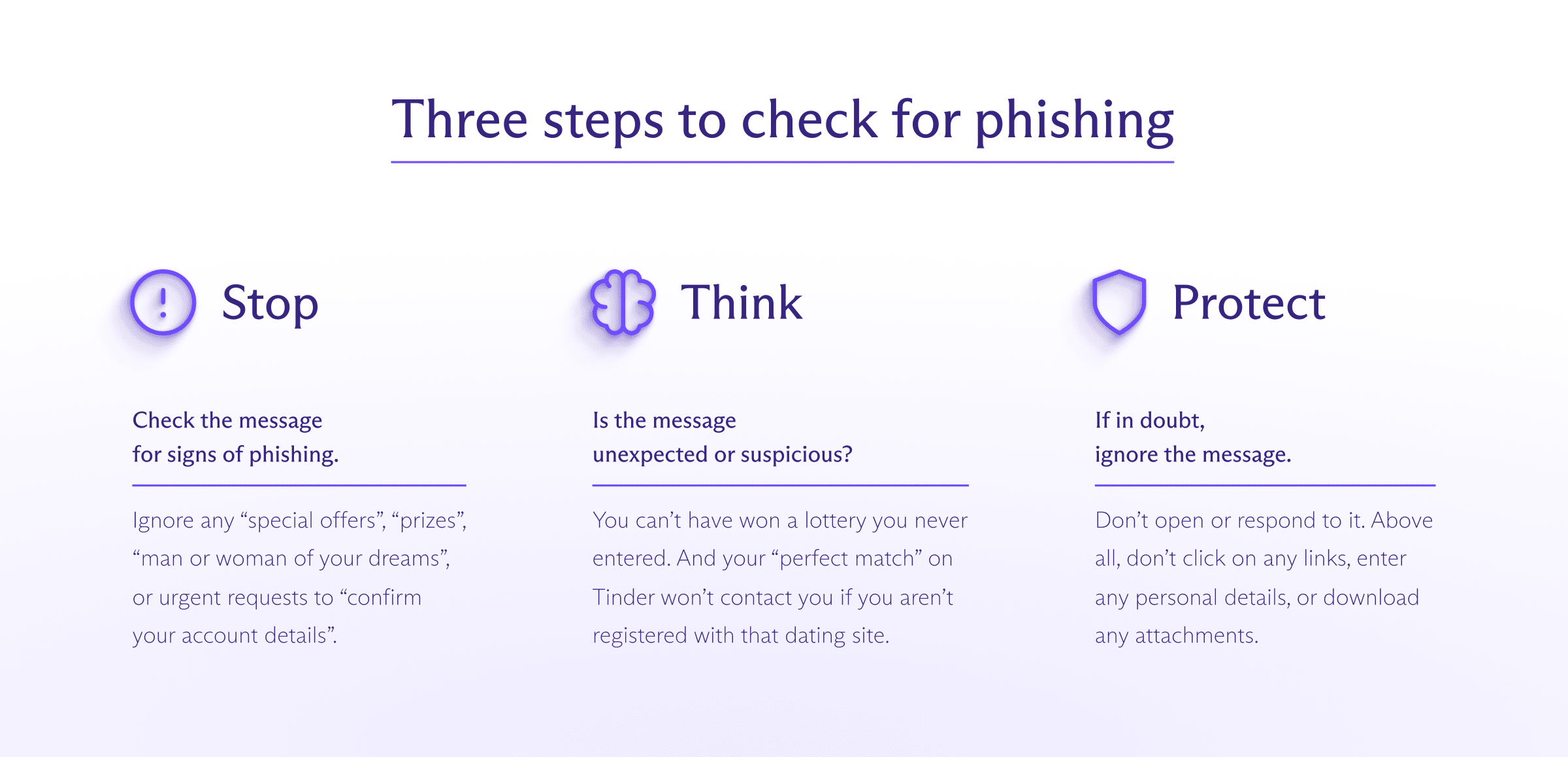
Remember that only fraudsters get in touch out of the blue and urge you to take immediate action or else. And legitimate companies won’t ask you for sensitive information by email.
If you’re concerned about an “urgent” message from your bank, for example, log in to your account or contact the bank directly to check. Only don’t use the contact details or login links in the message.
How to prevent phishing attacks
Being vigilant for signs of phishing is just one way to protect yourself against it. Here’s how to minimize the risk of phishing on all your devices:
1. Secure your email
Use a secure email provider with smart spam filtering, like Proton Mail. Proton Mail automatically filters spam into your spam folder and has PhishGuard advanced phishing protection, which flags potential phishing attacks.
We also make it easy for you to report phishing on the Proton Mail web and mobile apps.
2. Beware of links and attachments
Don’t click on links or download attachments in emails, text messages, or social media from unknown senders.
If you’re using a computer, you can hover your mouse over (don’t click!) a link to check the destination URL. In this fake UPS phishing email, the URL (https://zpr.io/xxx) clearly has nothing to do with UPS.
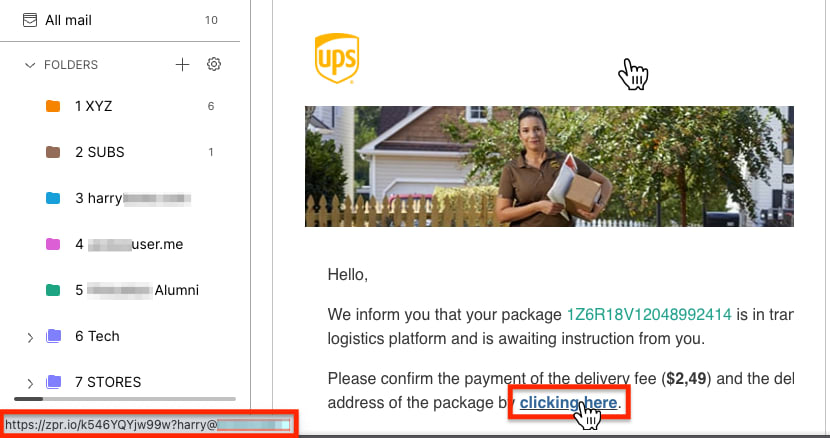
With Proton Mail, you can use link confirmation to check that email links are genuine, like this one from eBay UK (ebay.co.uk).

3. Don’t respond to spam
Don’t open spam messages or respond to them in any way. By replying to spam emails or SMS (for example, hitting unsubscribe or texting STOP), you’re only letting the spammers know that your email address or phone number is active. Delete them.
Opening emails can also allow email trackers to track you across the web. Get Proton Mail with enhanced tracking protection to block trackers.
4. Install antivirus software
Antivirus or internet security software may include spam filters to block potential phishing emails, and many subscriptions cover desktop and mobile devices. Make sure it’s from a reputable brand and updated with the latest virus and malware definitions.
If you do accidentally click on a phishing link and download malware, your security software may detect and disable it.
5. Keep your devices up to date
Keep your computer or phone operating systems, browsers, browser plug-ins, and other apps updated to the latest versions with security patches.
This can protect you against phishing that exploits operating system vulnerabilities.
6. Use strong passwords and 2FA
Make sure you use strong, unique passwords on all your online accounts. We recommend using a good, open-source password manager to help you create and remember strong passwords.
And enable two-factor authentication (2FA) wherever you can. That way, if your usernames or passwords are ever revealed through phishing, scammers won’t be able to access your accounts.
7. Back up your data
Make regular backups of your data, including offline backups. That way, you can always restore your data if your device is infected with ransomware or other malware that results in data loss.
Protect your business from phishing
Businesses in the US lost over $2.7 billion to business email compromise(new window) in 2022. Of the companies in the UK who reported a cyberattack in the same year, 83% said the attack was phishing(new window).
Fall for a phishing attack, and you could suffer a data breach or a ransomware attack. Apart from financial and data loss, that could damage your brand and customer trust.
So if you run a business, taking steps against phishing is vital for your cybersecurity. Here’s how to minimize the risk of phishing to your business:
Enable spam and phishing filters
Make sure you turn on spam and phishing filters in your email and internet security software.
Sign up for Proton for Business, and you’ll get Proton Mail with automatic spam filtering and PhishGuard advanced phishing protection enabled by default. Proton Mail also includes anti-spoofing for custom domains to prevent scammers from using your company domain for spam or phishing attacks.
Train your team
Run regular phishing awareness training with your employees so they know how to spot phishing. If you have the IT resources, you can send them mock phishing emails to give them practical experience. Make it easy for them to report suspected phishing.
Enforce strong passwords and 2FA
Make sure your IT systems enforce strong passwords and 2FA on all your team’s devices. If any of your team’s login details are revealed through phishing, 2FA will give you an extra line of defense.
Get corporate antivirus
If you have more than a couple of people on your team, consider getting enterprise cybersecurity software. Corporate antivirus solutions include real-time threat monitoring that focuses on endpoint security(new window) for whole networks, not just individual devices.
Protect critical data
Encrypt your business’s data to protect yourself. Consider Proton for Business, which secures your email, calendar, and online storage with end-to-end encryption. No one but you and those you authorize can access your data, even if your files are exposed in a data breach.
Back up your data
Make regular backups of your company’s critical information, including offline backups. That way, if a successful phishing attempt leads to data loss, you can always recover your information.
Stay safe against phishing
From bulk spam to targeted whaling, phishing remains one of the main ways scammers commit online fraud, and we’re all targets.
Since phishing relies on human error, vigilance is the best defense. If you receive a message with signs of phishing, don’t open or respond to it. Delete it.
But we’re all human, and even seasoned IT security experts can fall for phishing sometimes. That’s why you need to take steps to reduce the risk.
We’ve designed Proton Mail to give you the best chance against phishing, including:
- PhishGuard advanced phishing protection to flag potential phishing attacks
- Smart spam detection and custom filters to automatically filter spam
- Link confirmation to let you check links before opening them
- Domain authentication warnings to flag possible spoofed addresses and custom domain anti-spoofing to protect your domain from being spoofed
- Address verification to verify senders in end-to-end encrypted emails
- Aliases to hide your personal address from potential scammers
- Our Official badge to make it easy for you to identify which emails came from Proton
So beware of suspicious messages, get Proton Mail, and stay secure!

