A digital signature on a document is like a virtual fingerprint that verifies the identity of the person or entity that signed it.
Unlike handwritten signatures, which you can easily forge, digital signatures are highly secure because they’re protected by cryptography. Learn how digital signatures work and ensure the authenticity and integrity of digital messages, documents, and other data transfers.
What is a digital signature?
Digital signatures vs. electronic signatures
How do digital signatures work?
Are digital signatures secure?
What are digital signatures used for?
Authentication
Data integrity
Non-repudiation
Stay secure with digital signatures
Digital signature FAQs
What is a digital signature?
A digital signature is a cryptographic method that verifies the authenticity and integrity of digital documents, messages, or software.
Digital signatures are created with cryptographic algorithms and often appear as short tags appended to a document. They have numerous applications in various industries, from signing legal contracts to securing online banking, healthcare records, software distribution, and end-to-end encrypted email.
Like a handwritten signature on paper, digital signatures authenticate data but differ from physical signatures in the following ways.
Authentication
While handwritten signatures are often verified visually by comparing them to a reference signature, digital signatures are verified with signature verification algorithms, so they’re more difficult to forge. Verification only succeeds if the signature was created by the named signer on the verified document.
Handwritten signatures don’t depend on the signed data and always look the same. So you can just copy a physical signature to another document. By contrast, digital signatures are always a function of the signed data, so you can’t simply add them to another document.
Data integrity
Similarly, handwritten signatures only verify the signer’s identity, while digital signatures verify both the signer’s identity and the document’s integrity.
In short, a valid digital signature verifies that a document is from a known sender and hasn’t been tampered with since it was signed.
Digital signatures vs. electronic signatures
While the terms “digital signature” and “electronic signature (e-signature)(new window)” are often used interchangeably, they aren’t the same.
An e-signature is a broad legal category and can be as simple as a name on a digital document, depending on the jurisdiction. By contrast, a digital signature is a kind of e-signature that’s secured by cryptography.
How do digital signatures work?
Digital signatures use public-key cryptography(new window) (also known as asymmetric-key cryptography) to authenticate documents. This works by generating a mathematically related key pair:
- A private key, which is kept secret and used to create the signature
- A public key, which anyone can use to verify the signature
In simplified terms, here’s how signing and verifying works:
1. When a sender digitally signs a document, a hash function is used to create a “hash” of the data. A hash is a fixed-length string of numbers and letters like a digital fingerprint.
2. The hash is then signed with the signer’s private key, forming a digital signature that’s sent with the document.
3. The recipient receives the document, computes a hash from the received document, and uses the signer’s public key to verify the signature with the computed hash. If the signature verification algorithm accepts the signature, the computed hash, and the public key, the signature is valid.
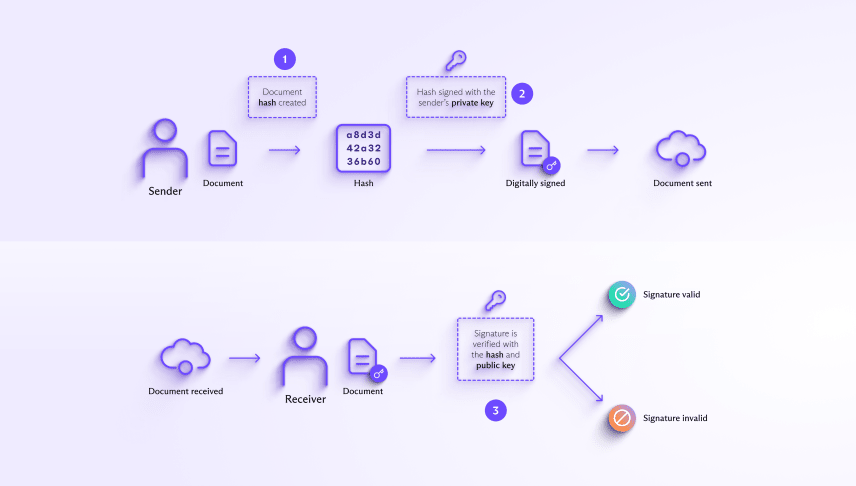
A valid digital signature verifies that the signed data came from the signer and hasn’t been altered.
Are digital signatures secure?
As digital signatures are cryptographically bound to the signed document, they’re much more secure than a handwritten signature or simple e-signature. Verifying a digital signature can only succeed if the same document is used for both signing and verifying.
But a digital signature’s security depends on keeping the signing keys secure. If the private key is stolen, an attacker can create digital signatures in the signer’s name.
Additionally, the verifier needs to know the identity of the signer that the public key belongs to. In other words, when you receive a digitally signed document, how can you be sure the public key you’re using to verify its digital signature belongs to the signer and not an attacker trying to impersonate them?
When you receive a digitally signed document, how can you be sure the public key you’re using to verify its digital signature belongs to the signer?
Public key infrastructure
One solution is to use digital certificates issued by trusted third-party organizations called certificate authorities (CAs). Digital certificates contain the public keys of individuals and organizations and verify that they belong to the certificate holder.
This system of CAs, known as public key infrastructure (PKI), helps ensure that the digital signature verification is trustworthy.
Proton Mail trusted keys
Another solution is to use PGP for digital signatures, or its open standard, OpenPGP. Unlike PKI, OpenPGP has a decentralized trust model where users can verify the identity of other users.
For example, with Proton Mail, you can mark a public key as trusted for each of your contacts. If that public key changes, you get a warning that sender verification has failed so that you can ask your contact whether they have indeed changed their public key.
If the sender’s identity is verified, you’ll see this lock symbol in the From address:

ProtonCA
Apart from verifying individual keys, OpenPGP also includes OpenPGP CA(new window), a system to verify the keys of email addresses under a given domain. At Proton, we’ve created a certificate authority called ProtonCA so that other providers and users outside Proton can more easily verify the keys of our users.

What are digital signatures used for?
Digital signatures perform three main functions in information security: authentication, ensuring data integrity, and non-repudiation.
Authentication
A valid digital signature verifies that the message came from the claimed sender, not an impostor. For example, we use digital signatures to verify addresses with trusted keys in Proton Mail, as discussed above.
Data integrity
Unlike a physical signature on paper, a digital signature can verify a document’s integrity. For example, we use digital signatures to verify that entries haven’t been tampered with in Proton Contacts.
Non-repudiation
As a digital signature is unique to the document and the signer, it provides a binding paper trail to the person who signed it. So if someone signs a contract with a valid digital signature and later claims they didn’t, the digital signature makes it difficult for them to disown (repudiate) it.
Given these three capabilities, digital signatures are used for various purposes, including secure email, financial transactions, legal and government documents, healthcare, cryptocurrencies, and software distribution — in short, any application where you need to ensure the authenticity and integrity of data.
Stay secure with digital signatures
You may use digital signatures manually to sign a document online like a traditional handwritten signature. For example, if you sign a job contract online, you’ll likely use a digital signature, which typically appears in a stylized font on the document.

But more often, digital signatures run automatically in the background, authenticating data transfers, for example, when you connect to your bank, update the software on your phone, or send an encrypted email.
At Proton, digital signatures are one way we ensure privacy and security in Proton Mail. We’re working to give everyone privacy and security online, so join us and stay secure!
Digital signature FAQs
Is digitally signing the same as encrypting?
Digital signatures use public-key cryptography(new window), but signing is different from encrypting.
- When you digitally sign data, you use your private key to create the signature, and the receiver verifies the signature using your public key. The main purpose of digital signatures is to verify who the data is from and check that it hasn’t been altered (authenticity and integrity).
- When you encrypt data, you use a person’s public key to transform it into unreadable ciphertext. The receiver uses their private key to decode it back into readable plaintext. The main purpose of encrypting data is to ensure that only authorized receivers can access it (confidentiality).
What’s a hash function?
A hash function is an algorithm that turns an arbitrarily sized message, like an email, document, or other data, into a unique, fixed-length string of numbers and letters called a “hash” (also known as “message digest”). Hash functions are used in digital signatures for two reasons.
- Most common digital signature schemes can only sign and verify small messages. So hash functions map arbitrarily sized documents to a small, fixed-sized message that can be signed with these schemes without affecting security.
- A cryptographic hash function is collision-resistant(new window), which means it’s hard to find two messages that produce the same hash. A change to the original message will result in a different hash. So a hash can be used to verify that data hasn’t been tampered with.
What’s a digital certificate?
A digital certificate contains the public key of an individual or organization and verifies that the key belongs to them. Most digital certificates are issued and digitally signed by a certificate authority.
What’s a certificate authority (CA)?
A certificate authority (CA) is a trusted third party that verifies the public key and identity of a person or organization. A CA either creates a public/private key pair for them or stores an existing key pair in their name.
Once a CA confirms a subject’s identity, it issues a digital certificate for the subject. You can then use the certificate to verify that a subject’s public key belongs to them.
What’s public key infrastructure (PKI)?
Public key infrastructure (PKI) comprises all the hardware, software, policies, and security systems used to issue, manage, store, and revoke certificates — all of which ensure that the digital certificate verification process is trustworthy. For example, certificate authorities store private keys in a hardware security module(new window) so they can’t be extracted (although this doesn’t prevent certificates from being mistakenly signed).
