What is end-to-end encryption (E2EE), and how does it work?
End-to-end encryption keeps your information private so only you and the person you’re communicating with can see it. Learn how it works and why it matters for your privacy.

What is end-to-end encryption?
End-to-end encryption (E2EE) encrypts your data on your device and only decrypts it on the recipient’s device. In “end-to-end,” one end is the origin (your device) and the other is the destination (the recipient’s device) of your data’s journey.
Without E2EE, your data can be decrypted along the way — for example, on a company’s servers — making it vulnerable to hackers, surveillance, and misuse. With E2EE, no one in between can read, scan, or share your sensitive information, not even the service provider.
How does end-to-end encryption work?
End-to-end encryption uses asymmetric cryptography to ensure only the intended recipient can decrypt your data. Each user has a public key (safe to share) and a private key (kept secret on their device).
When you send data, your device encrypts it with the recipient’s public key, producing unreadable encrypted data called ciphertext. This ciphertext can pass through multiple servers and networks without risk, because only the matching private key can decrypt it.
An example of end-to-end encryption
Imagine you’re sending your friend a locked box that only their key can open.
You lock your contents inside the box before sending it through the mail, and it stays locked as it travels through each postal checkpoint — the “servers.”
Anyone handling the box can see it, but they can‘t look inside or swap contents. Only your friend’s key can unlock it.
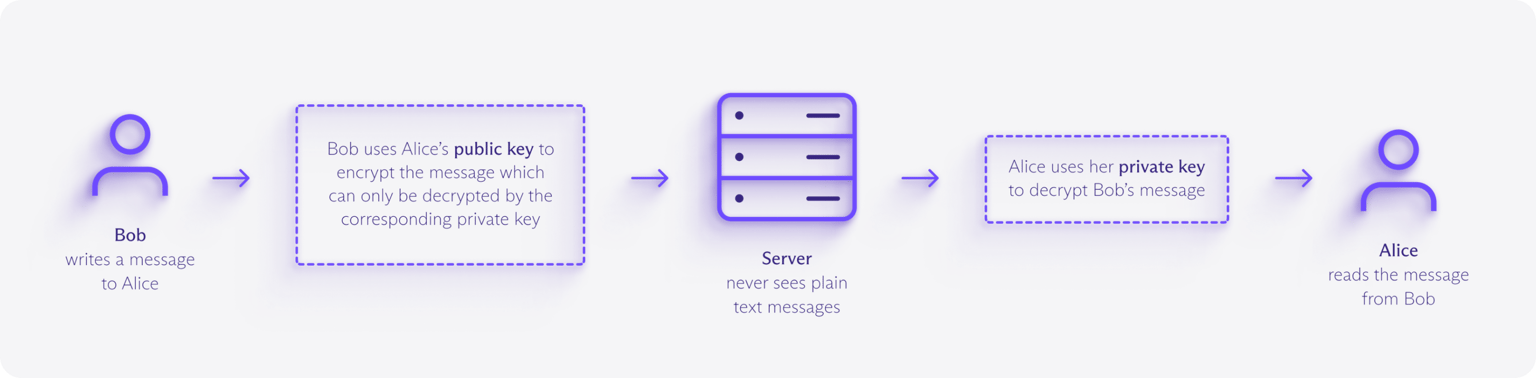
How is end-to-end encryption different from standard encryption?
Online services traditionally use in-transit encryption like TLS (the technology behind HTTPS) to encrypt your data while it’s traveling between your device and their servers.
This works well for browsing websites or submitting forms, as hackers or internet providers can’t see the sensitive information you input or receive.
But once your data reaches the company’s servers, it’s decrypted and stored using keys they control. That means they can read it, share it, or hand it over to governments or law enforcement if asked.
With E2EE, the company never holds the private keys, so they can’t read, scan, or share your content, even if they wanted to.
What are the benefits of end-to-end encryption?
Privacy
End-to-end encryption protects your email, photos, documents, and other files from scanning, profiling, or unauthorized access. Internet providers, advertisers, data brokers, and surveillance systems can’t monitor your content, giving you control over your personal information.
Security
Because the service handling the data doesn’t have the decryption key, you don’t have to trust it not to read, sell, or analyze your content. Even if its servers are breached, the stolen data remains unreadable. End-to-end encryption also preserves data integrity — your content arrives exactly as it was sent — and it complies with strict privacy regulations like GDPR and HIPAA.
Freedom
Private communication supports free expression. End-to-end encryption defends against censorship, surveillance, and political targeting, so you can share ideas and information without fear. Everyone needs this protection, but especially journalists, activists, and citizens under restrictive regimes.
Take charge of your data
Proton was built to protect your data from the start. With end-to-end encryption, open-source apps, and independent audits, your information stays yours.
Emails you send to other Proton users or to addresses that support PGP (an open standard for E2EE) are end-to-end encrypted, including the message body and attachments.
For other cases, you can add password protection. That way, only you and the person you’re writing to can read your emails.
Calendar events you create are end-to-end encrypted, including titles, descriptions, locations, and guest lists.
Even when you share your schedule or send an invite, no one else — not even Proton — can see who it’s for.
Passwords, usernames, web addresses, notes, credit cards, identity details, and other data you save are protected with end-to-end encryption.
When you share vaults, both the contents and the shared links are end-to-end encrypted, so only the people you invite can see what’s inside.
Everything you store and share in cloud storage is end-to-end encrypted, including file contents, file names, folder names, thumbnail previews, and shared links.
Only you and the people you choose to share with can access your files — not even Proton can see them.
Learn more about encryption