We often rely on cloud storage to keep and share files, such as personal photos, financial records, work documents, or confidential business data. If that information is sensitive, it needs to be protected.
Data breaches are more common and costly(new window) than ever, and a small mistake like sharing the wrong link or using a weak password can lead to serious consequences.
Whether you’re storing personal files or handling customer data for your business, it’s important to know how to keep that information secure in the cloud.
- What is sensitive data?
- Why should you protect sensitive data?
- Best practices for sensitive data protection and secure handling
- 1. Encrypt data before uploading
- 2. Share files using encrypted links
- 3. See what you’ve shared and revoke access anytime
- 4. Collaborate securely with shared folders
- 5. Restore previous versions of files
- 6. Use strong passwords and two-factor authentication
- 7. Monitor for unknown sign-ins and breaches
- 8. Build safe habits around shared data
What is sensitive data?
Sensitive data is any information that you wouldn’t want falling into the wrong hands, which could cause harm to you, a loved one, or your organization. Sensitive data typically includes:
- Personally identifiable information (PII), such as your full name, home address, email address, phone number, date of birth, and national ID, password, or driver’s license numbers.
- Financial information, including credit or debit card numbers, bank account details, tax identification numbers, and payment history.
- Health information (PHI), such as medical records, health insurance details, prescription history, diagnoses, and treatments.
- Authentication and access credentials, like passwords, security questions and answers, and biometric data such as fingerprints or facial scans.
- Confidential business information, including trade secrets, client data, internal emails or contracts, intellectual property, or strategic plans.
- Location or behavior data, such as GPS coordinates, browsing history, purchase history, and social media activity.
- Metadata, such as email sender and recipient, IP address, and timestamps. Photo metadata (EXIF) may reveal the GPS location, date and time, and device used.
Most types of files can contain sensitive information — documents, spreadsheets, photos, videos, audio files, emails, chat messages, and databases can all hold personal, financial, legal, or proprietary data. That’s why it’s important to treat all file types with care when storing or sharing them in the cloud.
Why should you prioritize sensitive data protection?
If you’re an organization, protecting digital data is essential, especially when it comes to the sensitive information of customers. Regulations like GDPR or HIPAA require you to keep certain data secure, and failing to do so can lead to serious penalties(new window).
Beyond compliance, a data breach can cost millions(new window), lead to lawsuits, and cause customers to lose trust and walk away. Internally, leaks of confidential business information can give competitors an edge or disrupt operations.
For individuals, keeping your data secure means keeping control over your life online and offline. If information like your home address or bank details gets leaked, it can be used for identity theft, fraud, doxxing(new window), or even physical threats. Beyond exposing your privacy, family photos can be used for AI training, invisible targeting, and exploited for ransom.
8 best practices for sensitive data protection and secure handling
Here’s what you can do to store sensitive data in the cloud and share it safely:
1. Encrypt data before uploading
For most cloud storage platforms, it’s important to encrypt files locally before uploading to ensure that your cloud provider can’t access your data. If it holds the encryption keys, your files could potentially be accessed by employees, exposed in data breaches, or handed over to third parties.
With Proton Drive, this step isn’t necessary. Your files — including metadata — are automatically protected with end-to-end encryption before they leave your device, so only you and the people you choose to share them with can access them.
2. Share files using encrypted links
When sharing sensitive files or private photos and albums, only the intended recipients should be able to access them. If you use unprotected or public links, anyone who obtains the link — either accidentally or by intercepting it — can view or download the files.
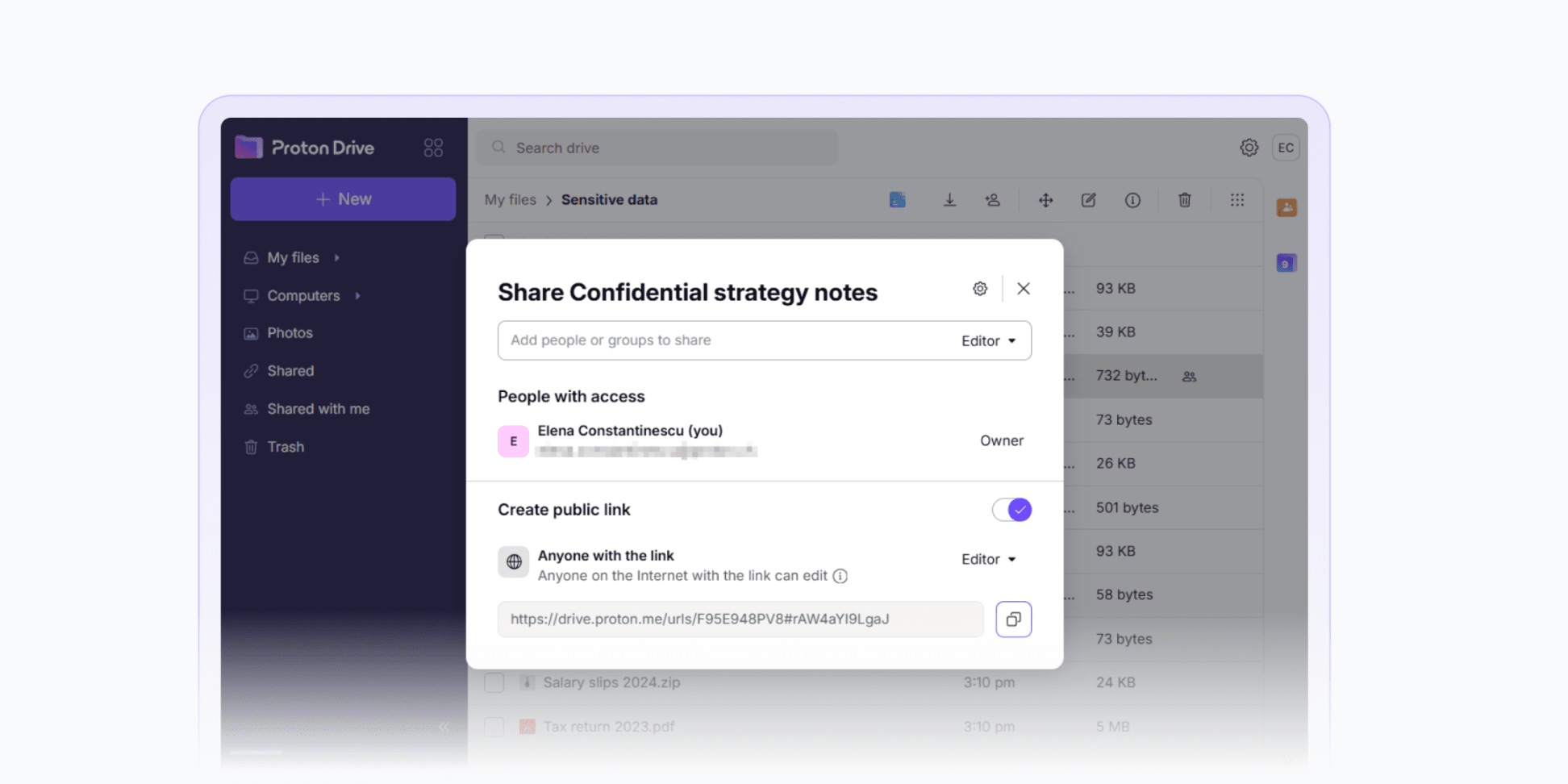
Proton Drive lets you generate secure public links, protect them with passwords, and set expiry dates. For greater control, you can share files privately via email invites, ensuring that only specific people or groups can access them.
3. See what you’ve shared and revoke access anytime
It’s important to remain in control after sharing sensitive information. Proton Drive makes this easy by grouping all your shared files in a dedicated Shared tab(new window), so you can quickly see what you’ve shared.
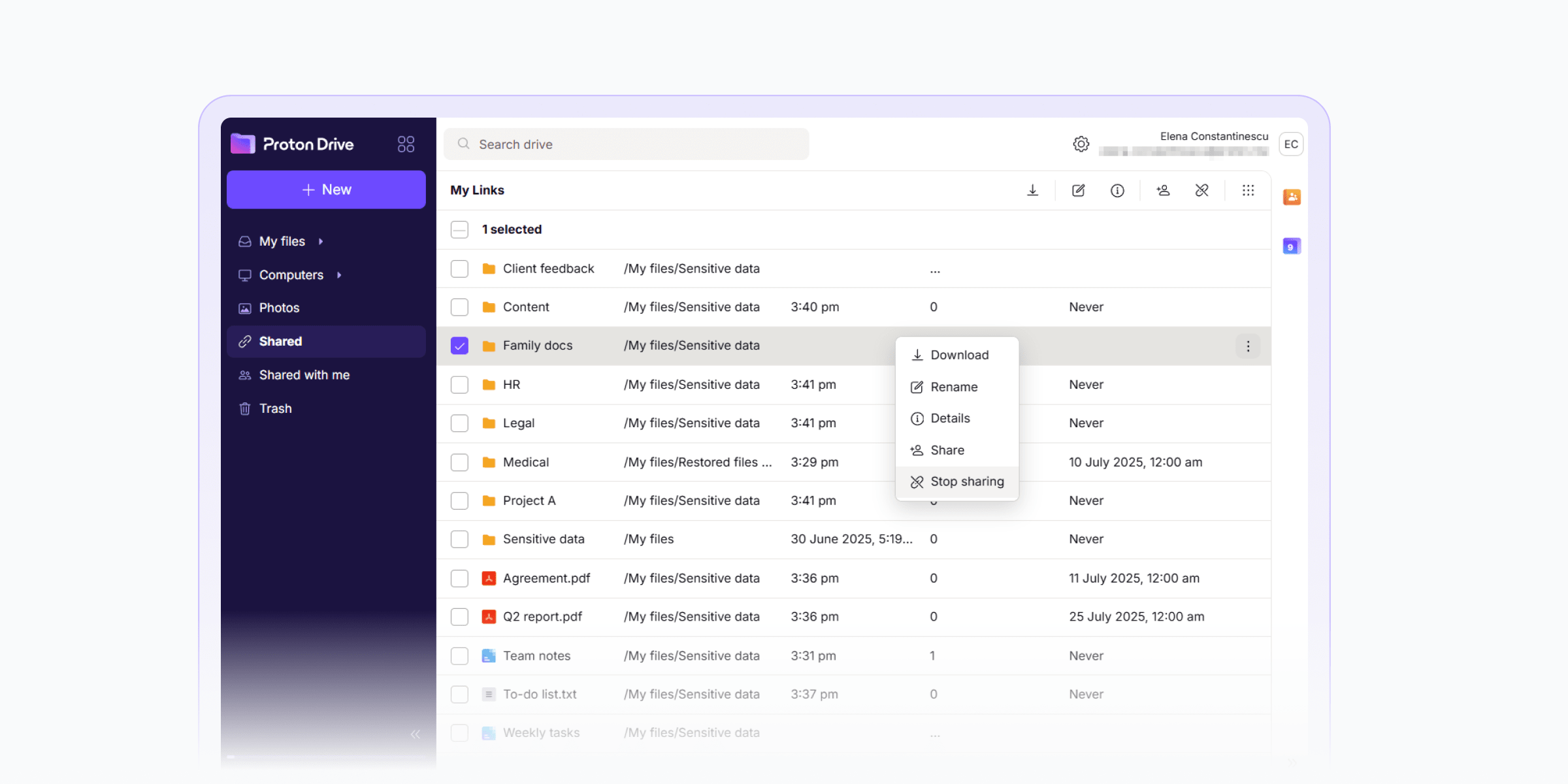
You can check how many times a link was accessed and revoke access anytime, whether it was shared via a link or email invite. If you disable a public link, the URL is permanently destroyed — re-enabling it creates a new, unique link, so old links can’t be reused.
4. Collaborate securely with shared folders
Giving several people access to your cloud storage folders is often necessary when working on sensitive documents, managing team files, or collecting information from clients — but maintaining control and security is key.
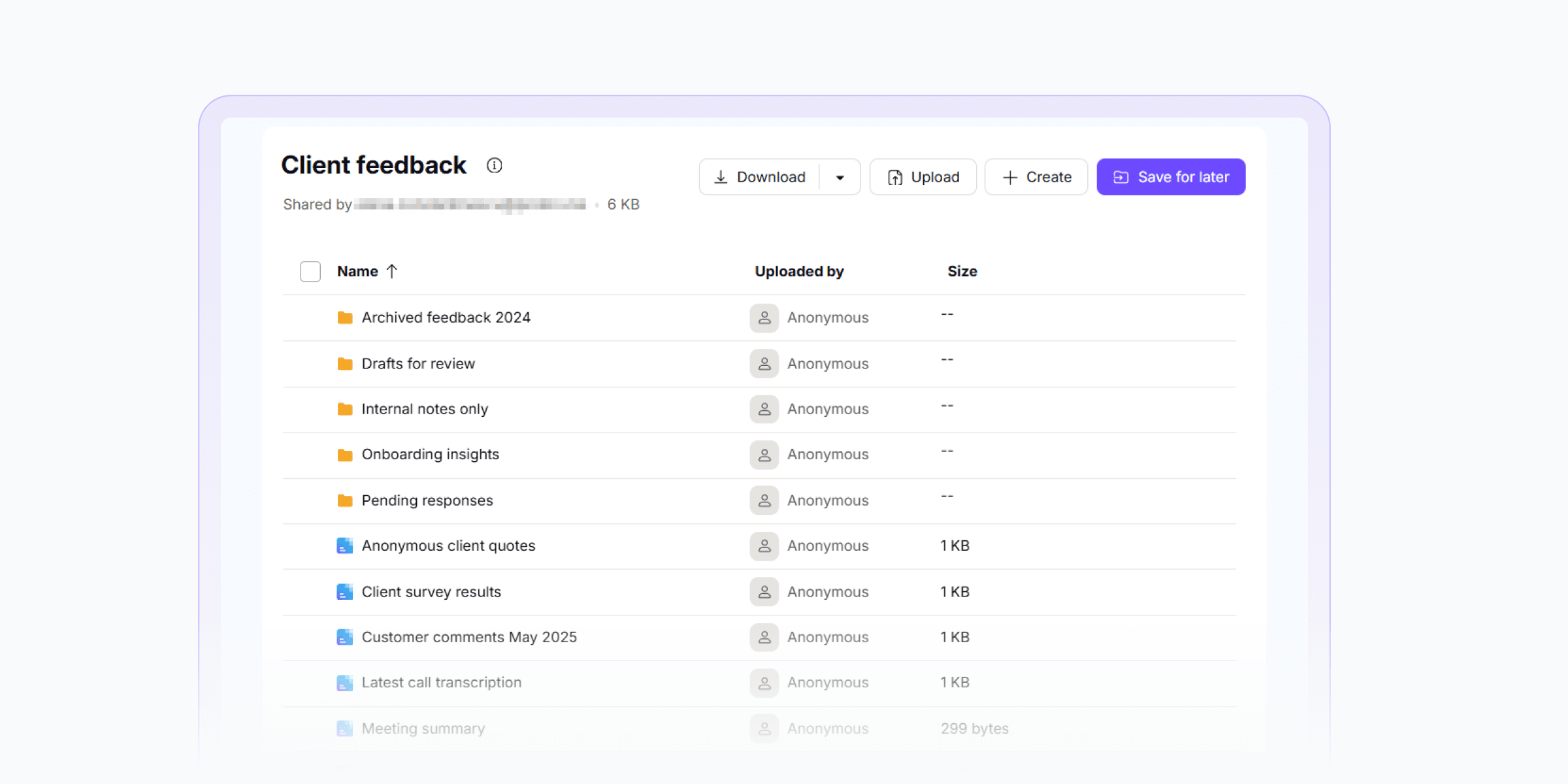
In addition to files, Proton Drive allows you to share entire folders and choose whether others have view-only or edit access — allowing them to upload or modify files if needed.
If you’re working on documents directly, you can use our online editor, which supports real-time collaboration features like commenting, suggestion mode, and live editing.
5. Restore previous versions of files
Mistakes, unwanted edits, or simply changing your mind can compromise data when working in cloud storage, especially when more people have access to the same folder and can overwrite files with their own versions.

Every time you upload or update a file in Proton Drive, previous copies are safely stored. You can view version history and restore an earlier copy if needed. Even after reverting, newer versions are still kept, so nothing is permanently deleted unless you choose to remove it.
6. Use strong passwords and two-factor authentication
No matter how secure your cloud storage provider is, your account is only as strong as your login credentials. A strong, unique password is your first line of defense against unauthorized access — and two-factor authentication (2FA) protects you even if your password is stolen or leaked in a data breach.
When signing up for a Proton Account, you can use our password generator to create a secure, hard-to-guess password — and set up 2FA using authenticator app or a physical security key to verify your identity at login.
If you’re on a Proton Business plan, you can enforce two-factor authentication across your team to make sure everyone in your organization is protecting their accounts.
7. Monitor for unknown sign-ins and breaches
Even with strong login security practices in place, it’s important to stay alert for signs of unauthorized access(new window) so you can act quickly if your account is targeted. Proton offers multiple tools to help you monitor and protect your account:
- Dark web monitoring alerts you if your email address or other personal data is found in known data breaches.
- A session manager shows all devices where you’re currently signed in, so you can revoke access to any session you don’t recognize.

- An activity monitor lets you track and audit authentication attempts across all Proton services, giving you insight into how and when your account is being accessed.
- Proton Sentinel automatically detects and blocks suspicious activity that could lead to account takeover.
8. Build safe habits around shared data
Human error can still compromise sensitive information. To stay secure, it’s important to build safe habits for yourself and for those you share data with, such as team members, clients, collaborators, and family:
- Be cautious of phishing emails or suspicious requests for access.
- Double-check recipients before sending links or granting folder permissions.
- Use passwords, expiration dates, and access controls when sharing sensitive files.
- Review access permissions regularly to ensure only the right people have the appropriate level of access, especially after team changes or finished projects.
- Review shared files and links regularly, as they often remain accessible long after they’re needed.
- Label sensitive files using clear naming conventions to stay organized, but avoid including private or confidential information in file or folder names.
Protecting sensitive information in the cloud is about using the right tools and staying vigilant. For individuals, it starts with free cloud storage, strong passwords, and careful sharing. For organizations, it means business cloud storage that supports access controls, compliance, and team-wide security practices.