Whether you’re backing up personal photos or searching for an easier way to share files with your team, cloud storage is an effective alternative to traditional methods like hard drives and USBs. With cloud storage, you can back up(new window), store, and access files and photos without relying on a physical hard drive.
This article explains what cloud storage is and how cloud storage works. We’ll also cover the benefits and risks of using it, especially concerns around data privacy and security.
- What is cloud storage
- How does cloud storage work
- Benefits of cloud storage
- Risks of cloud storage
- A privacy-focused cloud storage solution
- FAQ
What is cloud storage?
Cloud storage lets you keep your files, documents, photos(new window), and videos in “the cloud” instead of on a hard drive you own. Instead of saving your files on a local device, your data is stored offsite on remote servers that you can access over the internet.
Setting up your own cloud server for data storage is technically challenging and expensive, which is why most people opt to use a third-party cloud storage provider, such as Google Drive, Dropbox, or Proton Drive. Besides convenience, cloud storage providers also offer advanced security features like encryption and two-factor authentication (2FA) to help protect your files.
Because of the flexibility and accessibility of cloud storage, it is often used for:
- File backup: protecting data by creating secure copies that are stored offsite.
- Sharing and collaboration: enabling teams to work together in real-time.
- Secure data storage: storing sensitive data that requires advanced security measures.
How does cloud storage work?
When you upload a file to the cloud, your cloud storage provider duplicates it and stores copies on remote servers. As long as you have a device connected to the internet, you can sign in to your cloud service using a web browser or app to download or upload files.
Uploading data to the cloud
Here’s a simple explanation of the process of uploading your files if you use a privacy-focused, end-to-end encrypted cloud storage provider like Proton Drive. (Note: Providers like Google Drive and Dropbox always have the key to access your data, so the encryption step looks different for those services and is not as secure.)
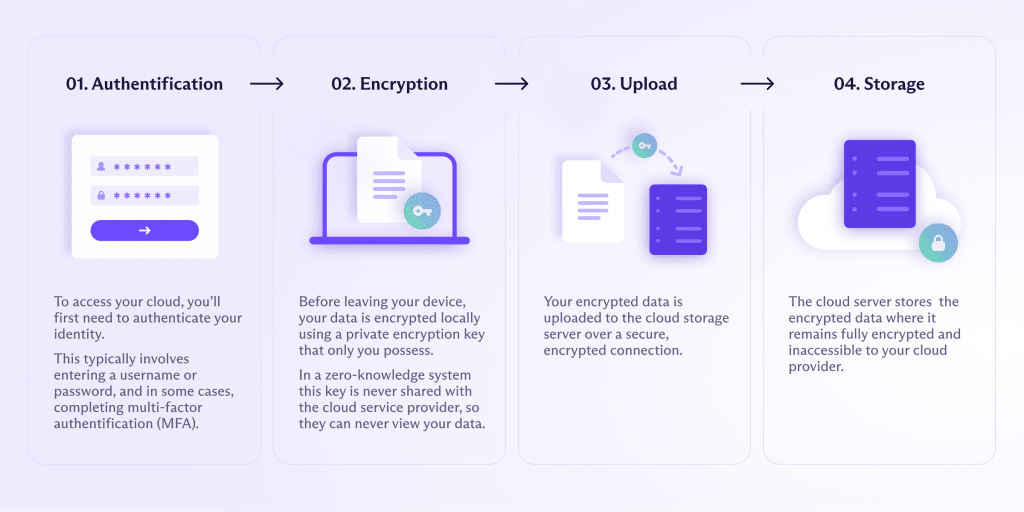
- Authentication: To access your cloud storage account, you’ll first need to authenticate your identity. This typically involves entering a username, password, and multi-factor authentication (MFA) code for extra security.
- Encryption: When you upload a file, your data is first encrypted on your device using a private encryption key that only you possess. In a zero-knowledge system, this key is never shared with the cloud service provider, so they can never view the contents of your files.
- Upload: Your encrypted data is then uploaded to the cloud storage server over a secure, encrypted connection.
- Storage: The cloud server stores the encrypted data where it remains fully encrypted and inaccessible to your cloud provider. Typically, cloud providers back up copies of the data on multiple servers to prevent data loss if something goes wrong.
Retrieving data from the cloud
To view or download your files from your cloud storage, the process basically goes in reverse:

- Retrieval: Your cloud server locates the encrypted data and prepares it for download. Your data remains encrypted at this point.
- Transfer: The encrypted data is transferred back to your device over a secure, encrypted connection, ensuring your files are safe against surveillance or data breaches during transit.
- Decryption: Once the encrypted data is received on your device, it is decrypted locally using the private encryption key that only you control.
- Access: You can now access and use your data in its decrypted form on your device. Any changes made can be re-encrypted and uploaded, following the same secure process.
Read a more technical explanation of how Proton Drive downloads your files
Types of cloud storage
There are multiple kinds of cloud storage, but they can fit into two categories: public and private. Proton Drive and Google Drive are examples of public cloud storage. Private cloud storage is usually set up by an organization for internal use. Here are some of the main differences between the two:
- Ownership: A private cloud is owned and operated by a single organization and only members of that organization have access to it. In a public cloud, you share the cloud service’s resources (for example, servers and network devices) with other people.
- Scalability: Public cloud storage is highly scalable and can easily accommodate many users and files. Private cloud storage is usually fixed and may require additional resources to expand.
- Security: Standard public cloud storage is considered less secure than private cloud storage due to its shared infrastructure. Since private cloud storage is only dedicated to a single organization, it can easily be customized to meet specific security requirements.
- Cost: Public cloud storage is generally cheaper than private cloud storage since the cost of maintaining the cloud is shared among its users. Private cloud storage also requires a significant upfront investment in hardware and resources.
Benefits of cloud storage
Cloud storage has become hugely popular in the last decade because of its benefits and flexibility. Here are some examples:
Backup and recovery
Cloud storage offers a secure and convenient way to back up important files, such as photos, videos, and documents. Even if your computer or phone is lost or damaged, you’ll have copies of your items in the cloud. This feature is especially critical for businesses.
Saving space
Local devices like laptops and mobile devices typically have limited storage capacity, and if you’re looking to store large files, you might run out of space. By using cloud storage, you can free up space on your local device and store these files in the cloud instead.
Data security
If you use a cloud storage provider that offers advanced security features(new window), you can protect your data from the moment you upload it to the moment you access it again. Features like end-to-end encryption or zero-knowledge architecture can ensure that only you and the people you permit will be able to decrypt your data.
Synchronization
One of the biggest advantages of cloud storage is the ability to keep files in sync across multiple devices and platforms. When you store files in the cloud, they’re accessible from any device with an internet connection, which means you don’t have to worry about transferring files manually. With Proton Drive, any changes you make to your file are also automatically updated in real time, ensuring you always have the latest version of your documents.
Real-time collaboration
Cloud storage document editors like Docs in Proton Drive(new window) allow multiple people to work on the same document simultaneously, reducing the need to send a file back and forth. Some cloud storage platforms also offer version control, which lets you track changes and revert to earlier versions of the document if needed.
Scalability
With physical storage devices like hard drives or USB drives, running out of space usually means buying additional devices or migrating all your data to a new device with greater capacity. Cloud storage lets you effortlessly grow your storage capacity alongside your needs. For example, you can easily upgrade from 500 GB to 1 TB of storage space with a few clicks.
Compliance
If you’re using cloud storage for business purposes, an end-to-end encrypted solution provides instant compliance with regulations such as HIPAA, CCPA, and GDPR as access to your data is securely restricted to you and the people you authorize. You can provide customers and clients with the confidence that their data is in safe hands.
Privacy protections
The location of a cloud storage data center can have significant legal implications. For instance, privacy-focused cloud storage providers often choose data centers in states with strong data protection laws — such as Switzerland. By using these cloud services, your data can benefit from these protections and remain outside of US or EU jurisdiction.
Risks of cloud storage
While cloud storage providers implement various security measures to protect your data, it’s important to remember that no system is completely foolproof.
Two of the most popular service providers are Google, which offers Google Drive, and Dropbox. Both allow you to store, manage, share, and collaborate on files in the cloud. However, both also have a poor reputation for privacy.
As per Google’s privacy policy, the big tech giant can access and analyze your data and share your information with third parties, including for government surveillance. Similarly, Dropbox can share the data you store with third parties, and the company has a history of security issues, including compromised passwords and resurrected data (in which deleted files reappeared).
While these risks are not limited to Google and Dropbox, they demonstrate the potential consequences of using cloud services provided by companies that (1) do not prioritize your privacy and, as a result, (2) do not provide end-to-end encryption by default.
Like many cloud storage providers, both Google and Dropbox use a method of encryption that only applies in transit and at rest. This means that when your data sits on the service provider’s servers, they can decrypt it and use your data as they please. It also makes your data more accessible to bad actors who gain unauthorized access to those servers.
The best way to defend the integrity of your files and prevent unauthorized access is to use a reputable and trustworthy end-to-end encrypted cloud storage provider like Proton Drive. With end-to-end encryption, you hold the only key that encrypts and decrypts your data and have total control over who else can be authorized to do so. Paired with a zero-knowledge architecture, Proton couldn’t gain access to your data even if we wanted to.
A privacy-focused cloud storage solution
Proton Drive was created by the same team that developed Proton Mail(new window) and Proton VPN(new window) (and uses the same end-to-end encryption (E2EE) to secure your files. This means nobody, not even Proton, can access them without your permission. All your files are encrypted locally on your device before being uploaded to our cloud servers.
With Proton Drive, you can enjoy the benefits of cloud storage without compromising your privacy. Your information remains safe, secure, and accessible only to you and the people you choose.
For businesses, Proton Drive’s encryption and ease of use provides simple compliance with data protection regulations, and dedicated business plans make it easy to get your team up and running with secure cloud storage in minutes.
Our cloud storage also gives you access to Docs in Proton Drive, which lets you create and collaborate with others in real time on end-to-end encrypted documents. Additional features include:
- Secure sharing links(new window) with the ability to add passwords(new window) or expiration dates
- Sharing via email so you can control access and permissions on your files
- Photo storage(new window) with automatic mobile backups
- Large file sharing with no size limits
Proton was built on the belief that your data belongs to you and that nobody should be able to exploit it. If you’d like to learn more about our mission and why we build privacy-first services, check out our story(new window) and impact(new window).
FAQ
How do I access cloud storage?
Accessing cloud storage depends on your cloud storage provider, but in general, there are a few common steps:
– Register for a cloud storage service, such as Proton Drive.
– Sign in to your account on your cloud provider’s website. Alternatively, you can also download the mobile app.
– Select which files and folders you want to store in the cloud and upload them.
– Many cloud storage services allow you to share files with others by creating a link or inviting them to access your files directly. You can also set permissions to control who can view or edit your files.
Is cloud storage safe?
Most cloud storage providers encrypt your files with TLS and AES-256. These encryption methods are widely considered secure and can protect your files from interception and tampering by third parties, but your cloud provider still retains your private key. This means your cloud provider can access your files if necessary (for example, in response to a legal request or a security incident). A hacker who breaches your cloud storage provider’s servers can also easily steal your private key and access your files.
The best way to defend the integrity of your files and prevent unauthorized access is to use a reputable and trustworthy end-to-end encrypted cloud storage provider like Proton Drive.
Can anyone see your cloud storage?
In general, no one can see your cloud storage unless you specifically share your files with others. However, bear in mind that most cloud storage services store your private key alongside your data, which means your cloud provider can access your files at any time. If your cloud provider’s servers are breached, a hacker can also easily obtain your documents.
To guarantee the privacy of your files, choose a cloud storage provider that uses end-to-end encryption — the only type of encryption that prevents unauthorized third parties from accessing your files.
Is cloud storage free?
Most cloud storage services offer a free plan that gives you one or two gigabytes of free storage. With Proton you can enjoy 5 GB of free cloud storage. You can upgrade to a paid subscription for additional storage space.
